Cybersecurity Essentials have evolved from a specialized IT concern into a core business discipline that governs trust, resilience, and long-term success. In the Technology Era, where devices, cloud services, and digital processes touch every corner of the organization, strong security practices are no longer optional. This guide outlines the core elements every organization and individual should understand to protect themselves, their data, and their customers. By focusing on practical, implementable steps, anchored by data protection and threat detection, you can build a robust defense that scales with digital ambitions. Whether you are new to security or seeking to elevate your program, these essentials offer a clear path to improved safety and confidence.
Framed differently, these same concepts form a structured framework of digital safety and cyber risk management that guides decisions across technology, people, and processes. LSI-driven phrasing favors terms like information security foundations, protective controls, and a defense-in-depth mindset to communicate the same ideas. A robust security posture emerges when people, processes, and technology align under governance, continuous monitoring, and prepared response playbooks. In practice, IT teams translate these concepts into practical steps, such as training programs, policy development, and incident-ready workflows, that empower every user to contribute to safety. As the landscape evolves, the emphasis remains on prevention, detection, and rapid recovery, using language that resonates with diverse audiences while preserving the core intent.
Cybersecurity Essentials for the Technology Era
In the Technology Era, cybersecurity transcends IT silos and becomes a strategic driver of trust, resilience, and long‑term success. Organizations must weave cybersecurity essentials into governance, operations, and culture, guided by practical actions anchored in cybersecurity best practices.
A pragmatic approach centers on data protection, threat detection, and a clear risk assessment process that prioritizes people, processes, and technology. By tying security outcomes to business goals, leadership can measure progress, allocate resources effectively, and scale defenses as digital ambitions grow.
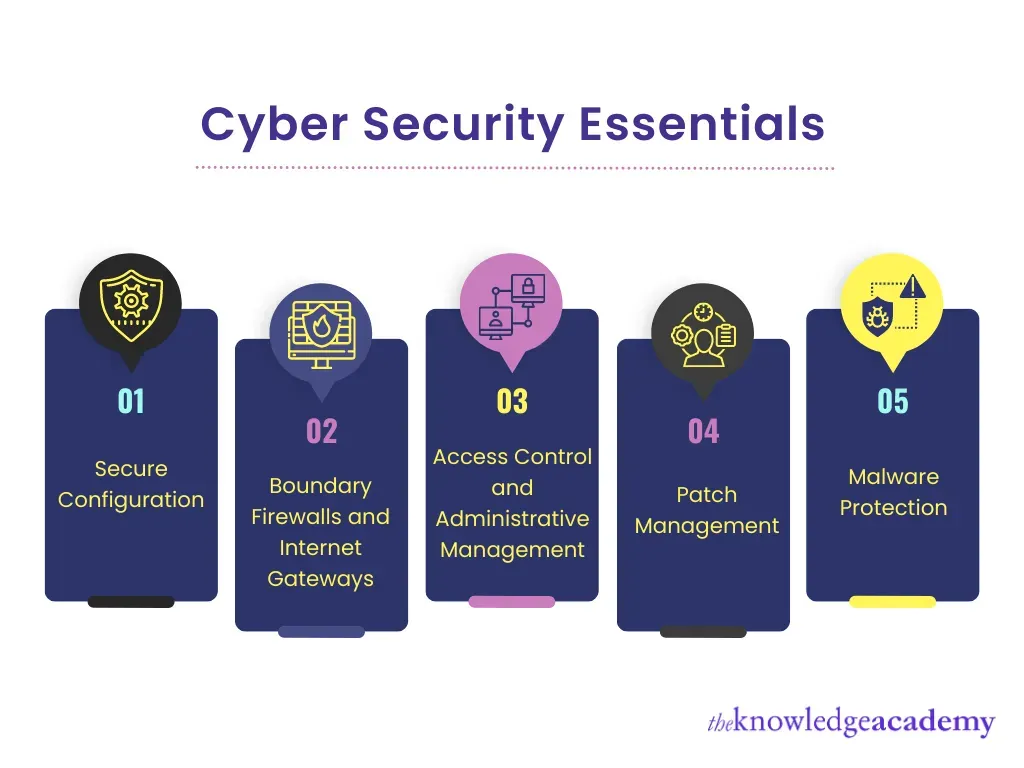
Identity, Access, and Privilege: Enforcing Least Privilege
A secure foundation starts with who can access what, when, and how. Implementing multi‑factor authentication (MFA), role‑based access control (RBAC), and just‑in‑time access reduces the risk of unauthorized entry and credential abuse, which are common attack vectors.
Regularly reviewing permissions and automating provisioning align with cybersecurity best practices, strengthening data protection and reducing the likelihood of privilege creep. A risk‑aware mindset ensures access controls stay current as personnel and systems evolve.
Data Protection: Encryption, Classification, and Backup
Data protection sits at the heart of security. Encryption at rest and in transit shields information even when systems are compromised, while data classification informs the level of protection each data type requires.
Robust backup strategies, tested restoration procedures, and ongoing recovery planning ensure resilience against incidents such as ransomware or hardware failures. This discipline supports risk assessment outcomes by providing reliable recovery paths for vital data.
Secure Engineering and Patch Management
Secure engineering embeds security into the software development lifecycle, from design reviews to secure coding standards and automated testing. A proactive approach reduces the introduction of vulnerabilities and strengthens the surface that threat actors may target.
Patch management accelerates remediation of known flaws through staged testing, prompt deployment, and comprehensive remediation tracking. By aligning patch practices with threat detection capabilities, organizations minimize risk without hampering productivity.
Threat Detection, Incident Response, and Recovery
Continuous monitoring, threat detection tooling, and real‑time telemetry enable rapid identification of anomalies and potential breaches. An integrated approach—EDR/NDR, SIEM, and well‑defined alert playbooks—speeds investigation and containment.
A documented incident response plan, regular tabletop exercises, and clear roles help reduce chaos during events. A strong recovery program, including business continuity and disaster recovery, minimizes downtime and protects customers and stakeholders.
Security Awareness, Culture, and Training
Human behavior remains a leading risk factor, making security awareness training essential. Phishing simulations and practical guidance empower users to recognize and avoid common attack vectors.
Cultivating a security‑minded culture—supported by leadership and ongoing learning—turns secure habits into the default. When people are informed and engaged, cybersecurity best practices and data protection become everyday standards across the organization.
Frequently Asked Questions
What are Cybersecurity Essentials and why are they the foundation of cybersecurity best practices for data protection?
Cybersecurity Essentials are the core controls every organization should implement to protect people, data, and systems. They center on identity and access management (MFA, RBAC), data protection through classification and encryption, threat detection, risk assessment, and security awareness training. Start by prioritizing critical assets, applying strong access controls, classifying data, enabling encryption, establishing backups, and deploying monitoring and training programs.
How does risk assessment fit into Cybersecurity Essentials and guide prioritization of controls?
In Cybersecurity Essentials, risk assessment identifies critical assets, threats, vulnerabilities, and current safeguards. It helps prioritize remediation by risk level, informs budgeting and governance, and ensures controls align with business objectives. Regular reassessment keeps protections current.
What role does threat detection play in Cybersecurity Essentials?
Threat detection is the continuous monitoring layer of Cybersecurity Essentials. It uses SIEM, EDR/NDR, and log analysis to identify suspicious activity and trigger incident response. Regular testing and clear alert triage improve response times and containment.
How should data protection be implemented within Cybersecurity Essentials?
Data protection in Cybersecurity Essentials means classifying data, encrypting at rest and in transit, and maintaining tested backups. Governance decisions define retention and secure disposal to minimize risk, even during incidents.
Why is security awareness training essential in Cybersecurity Essentials?
Security awareness training reduces human risk, a leading threat vector. It should include phishing simulations, straightforward guidelines, and leadership commitment to foster a security-conscious culture. Ongoing education strengthens the human layer of defense.
How can you measure the success of a Cybersecurity Essentials program?
Track metrics such as mean time to detect (MTTD), mean time to respond (MTTR), patch deployment velocity, data recovery time, and the percentage of systems with up-to-date protections. Regular security reviews and maturity assessments support continuous improvement and adherence to cybersecurity best practices.
| Area | Key Points |
|---|---|
| Landscape (Cybersecurity in the Technology Era) | Cloud-native shifts, remote work, and interconnected systems expand the attack surface. Attackers exploit misconfigurations, weak credentials, outdated software, and unmonitored systems. Regulations and customer expectations demand stronger data protection and transparent governance. Cybersecurity essentials become a continuous obligation, blending technology, process, and people to form a resilient security program. |
| 1) Identity, Access, and Privilege | Principle of Least Privilege; IAM practices with MFA, RBAC, and just-in-time access. Enforce MFA on critical systems; regularly review permissions; remove stale accounts. Automated provisioning/de-provisioning ensures right access at the right times. |
| 2) Data Protection: Encryption, Classification, and Backup | Classify data; apply encryption at rest and in transit; implement robust backups tested regularly. Data protection is a governance issue—define retention and secure controls for data. |
| 3) Secure Engineering and Patch Management | Embed security in the SDLC; follow secure coding standards and automated testing. Accelerate remediation with patch management, staging, prompt updates, and tracking. |
| 4) Endpoint Security and Network Visibility | Protect endpoints and monitor networks with EDR/NDR and SIEM for real-time telemetry. Use clear alert triage workflows and playbooks to shorten detection-to-response time. |
| 5) Threat Detection, Incident Response, and Recovery | Continuous monitoring, incident response planning, and tabletop exercises. Documented IR plans, defined roles, and communication with stakeholders. Recovery planning links to business continuity and disaster recovery. |
| 6) Security Awareness, Culture, and Training | Ongoing awareness training, phishing simulations, and clear guidelines empower users. A security-first culture, reinforced by leadership, makes secure habits the default. |
| 7) Governance, Compliance, and Risk Management | Align with standards (NIST, ISO/IEC 27001) and privacy laws. Formal risk assessment identifies assets, threats, vulnerabilities, and controls to prioritize remediation. |
| Building a Practical Cybersecurity Program | Start with a prioritized blueprint balancing risk, cost, and impact. Actionable steps: map critical assets, establish robust IAM, enforce data protection, harden the software supply chain, invest in visibility (SIEM, EDR/NDR, SOC), develop and exercise an incident response plan, train the workforce, and integrate governance and risk management into strategy. |
| Measuring Success and Continuous Improvement | Track metrics like mean time to detection (MTTD), mean time to respond (MTTR), patch velocity, data recovery time, and protection coverage. Regular reviews, audits, and maturity assessments drive iterative improvement. |
| Common Challenges and How to Address Them | Budget constraints, complex environments, talent shortages, and balancing security with user experience. Mitigations include prioritizing high-impact controls, automation, managed services, training, and risk-based approaches. |
| The Role of Emerging Trends in Cybersecurity Essentials | AI/ML-informed defense, Zero Trust, continuous authentication, and AI-assisted threat hunting augment core practices. Resilience-focused design complements prevention in the Technology Era. |
Summary
Conclusion will follow after the table.